How To Use Remote Iot Behind Router Without Windows
Can you truly harness the power of the Internet of Things (IoT) without the constraints of a Windows operating system, especially when dealing with devices tucked behind a router? The answer is a resounding yes, and the possibilities are surprisingly broad and elegantly achievable. The assumption that Windows is a necessary gatekeeper for remote IoT access is a misconception. In today's interconnected world, leveraging IoT devices from afar without relying on a Windows interface is not just feasible, it's often the more practical and secure approach.
The focus shifts away from Windows-centric configurations and embraces a more versatile ecosystem. Think of it as liberating your IoT devices from a single point of control and extending their reach through a web of accessible platforms. The advantages are manifold: enhanced security by reducing reliance on potentially vulnerable Windows systems, increased flexibility in terms of device compatibility and geographical access, and a significant reduction in the overhead associated with maintaining a Windows-based remote access solution. The core of this approach lies in understanding the fundamental concepts of networking and the tools available to facilitate remote access.
Let's dive into the essential elements of establishing remote IoT access independent of Windows. The core principle revolves around bypassing the Windows environment altogether and instead focusing on direct communication with your IoT devices via your router and the internet. This requires a strategic combination of hardware and software that speaks the universal language of the web. The key components include the IoT devices themselves, the router (acting as the gateway), a method of external access (such as a dynamic DNS service or a static IP address), and a secure communication protocol. Before getting hands-on with these elements, it is crucial to understand the purpose and function of these items.
First, let's discuss the IoT devices. These are the workhorses of your remote monitoring and control system. They can range from simple sensors gathering data (temperature, humidity, motion) to more complex actuators controlling appliances or industrial equipment. The design of your IoT devices' role is contingent on how these units will be used, the complexity of this network of devices will define the method by which they will connect to your network. They communicate using various protocols, including Wi-Fi, Bluetooth, Zigbee, or even wired connections. The critical aspect is ensuring these devices have an IP address, either assigned dynamically by your router (DHCP) or statically configured. Dynamic IP addresses are a common choice for the majority of devices and services, however, static IP addresses are preferable when you plan to make the device remotely accessible. This ensures the device has a fixed address on your local network, which is essential for consistently locating it from the outside world. This is crucial for remote access.
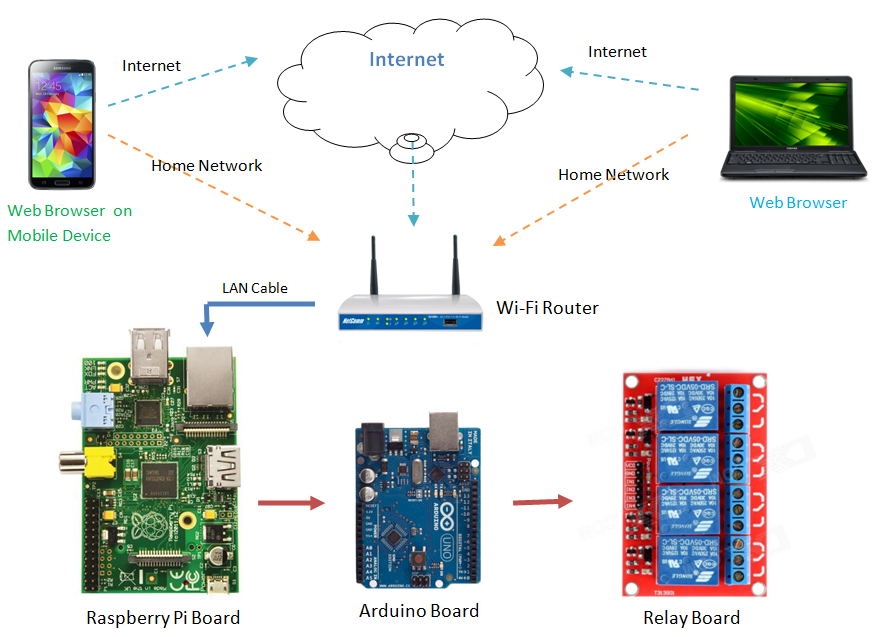
The router is the linchpin of this system, acting as the intermediary between your local network and the wider internet. It's the traffic controller, directing data packets to their intended destinations. Your router's configuration is paramount to establishing remote access. It involves setting up port forwarding rules and possibly implementing a Dynamic DNS (DDNS) service. Port forwarding effectively creates a pathway through your router's firewall, allowing external requests to reach specific devices on your local network. The specific ports that you need to forward will depend on the services or protocols your IoT devices use (e.g., port 80 for HTTP, port 22 for SSH). Dynamic DNS services, on the other hand, solve the problem of a dynamically changing external IP address. Your internet service provider often assigns a dynamic IP address. DDNS services track and update your public IP address, associating it with a hostname that remains consistent, simplifying remote access since you don't need to remember your ever-changing IP address.
The choice of your operating system, as it would appear on first glance, is crucial, but in truth, it is less critical than the configuration of the router and the method by which you plan on accessing the IoT devices. The router doesn't use a Windows operating system to function, the IoT devices are most likely running a lightweight operating system to handle the processing of data. The operating system that's used to access these devices could be anything from Android, to MacOS, to Ubuntu, or any other operating system that allows remote connections. This allows you to select the operating system that best fits your security needs, the type of remote access you require, and the ease of use of these systems.
Security is non-negotiable when dealing with remote access. It's important to shield your devices from unauthorized access. Start with a strong, complex password for your router's administrative interface. Enable the router's firewall to block unsolicited incoming traffic. Implement secure communication protocols, such as HTTPS for web-based access or SSH for command-line access. SSH (Secure Shell) is a network protocol that provides a secure channel over an unsecured network. It is a well-established method for remote access to command-line interfaces, and it offers robust encryption, making it a safe way to manage devices from a distance. You can also utilize a Virtual Private Network (VPN). A VPN creates an encrypted connection between your device and your home network, effectively extending your home network to your remote location. This adds an extra layer of security and allows you to access your devices as if you were physically present at home. Regularly update the firmware of both your router and your IoT devices to patch security vulnerabilities. And if possible, avoid exposing services directly to the internet. Instead, use a VPN or reverse proxy to securely access your devices.
Let's delve a bit deeper into setting up remote access using different approaches. One of the more accessible methods is using a web server on an IoT device or a dedicated server on your local network. If your IoT device has web-based capabilities, which is increasingly common, you can access it through your browser. This involves port forwarding on your router to direct external traffic (typically on port 80 or 443) to the device's IP address. You will need to set up a domain name or use your IP address along with the port to make the connection, such as `http://yourdomain.com` or `http://your_ip_address:80`. Another approach involves using SSH for command-line access. SSH is particularly well-suited for managing devices that don't have a graphical user interface. With port forwarding enabled, you can connect to the device using an SSH client from anywhere. Then, youll access the device via a terminal session.
Another option is to use a VPN. Setting up a VPN server on your router or on a separate device on your network is generally a good choice. Once connected to the VPN, you'll have full access to your local network, including your IoT devices. VPNs provide a higher level of security and make management much easier. This is a secure connection between your device and your home network, creating a secure tunnel for all of your network traffic, allowing you to access your IoT devices as if you were physically at home.
Let's now look at some popular platforms and services you can use. For Dynamic DNS, services like No-IP, DynDNS, or Duck DNS are widely used and provide simple ways to create a hostname that always points to your current IP address. When choosing a DDNS provider, consider factors like cost, ease of use, and whether they support your router model. For web-based access, platforms like Home Assistant or OpenHAB can be incredibly powerful. These are open-source home automation platforms that offer a centralized interface for managing various IoT devices. They often support secure remote access, making them a great choice for beginners and experienced users alike. If you need a more lightweight solution, Node-RED is a flow-based programming tool that can be used to connect IoT devices. You can deploy Node-RED to a Raspberry Pi or other small devices and build custom dashboards and automation rules. This can be accessible via the web using secure protocols like HTTPS.
Let's examine a practical example. Imagine you have a Raspberry Pi with a temperature sensor connected to your local network. You can establish remote access to this system without relying on Windows. First, assign a static IP address to the Raspberry Pi on your network. Then, set up port forwarding on your router, forwarding traffic on port 22 (SSH) to the Raspberry Pi's IP address. You can install a DDNS client on the Raspberry Pi or your router to allow easier access to the device via a consistent URL. Next, configure a VPN server on your router to encrypt all communications to and from the device and ensure your data is secure. Then, from anywhere in the world, you can SSH into the Raspberry Pi using its hostname or the DDNS-provided URL, and manage the device through the terminal. Alternatively, if the Raspberry Pi is running Home Assistant or a similar platform, you can securely access its web interface via the VPN or use its remote access features.
The advantages of avoiding Windows in this context are significant. It reduces your attack surface by removing a potentially vulnerable operating system from the remote access path. It enhances flexibility, allowing you to access your devices from any operating system that supports the relevant protocols (e.g., SSH, web browsers). It also simplifies maintenance, as you don't need to deal with Windows updates, compatibility issues, or the overhead associated with running a Windows-based server solely for remote access.
When troubleshooting, consider the following common issues. First, double-check your port forwarding rules on your router, ensuring the correct ports and the correct IP address are configured. Firewall settings on your router or on the IoT devices may be blocking the incoming traffic, so be sure to examine this. Second, verify your DDNS settings. Ensure the hostname is up-to-date and correctly reflects your public IP address. Test the hostname from outside your local network. Third, check your internet connection. A poor internet connection can hinder remote access. Make sure your connection is stable, and the bandwidth is sufficient for your needs. Finally, check the IoT devices themselves. Are they online and connected to your local network? Verify the network configuration settings on your IoT devices to make sure they are correctly connecting.
The landscape of remote IoT access is continuously evolving. Emerging technologies and standards will continue to provide more efficient, secure, and user-friendly methods for accessing and managing IoT devices remotely. Keep an eye on trends like the increased adoption of edge computing. Edge computing involves processing data closer to the source. It reduces latency and improves reliability, and this will increase the possibilities of remote IoT capabilities. Also, look out for the development of more standardized protocols and platforms that offer simpler setup and enhanced security. Finally, be sure to always remain informed about new security practices and the latest security threats that can compromise IoT devices. A proactive approach to security is vital to secure your IoT network.
In conclusion, the journey to accessing your IoT devices remotely, without Windows, is entirely achievable and often more advantageous. By understanding the core concepts of networking, router configuration, security, and available platforms, you can create a robust and accessible system. The choice of operating system is less important than the choices made in network design and the methods employed for secure communication. Embrace the possibilities beyond the Windows operating system and experience the true potential of your IoT devices.