Ssh Iot Over Internet Aws
Could the convergence of SSH, IoT devices, and the cloud, specifically AWS, be the key to unlocking unprecedented levels of security and control in the interconnected world? The answer, increasingly, appears to be a resounding yes, as this trifecta offers a potent combination for managing and protecting Internet of Things deployments, even across vast and complex networks. The inherent power of Secure Shell (SSH) for secure remote access, coupled with the flexibility and scalability of AWS, provides a compelling architecture for securing and managing the myriad devices that constitute the IoT landscape.
The rapid proliferation of Internet of Things (IoT) devices has created both opportunities and vulnerabilities. These devices, ranging from simple sensors to complex industrial equipment, are often deployed in remote and challenging environments, making them prime targets for cyberattacks. Securing these devices and maintaining their operational integrity is paramount. This is where SSH, used as a secure communication protocol, becomes invaluable. SSH provides a secure channel for remote access, allowing administrators to configure, monitor, and troubleshoot devices without exposing them to the open internet. Coupled with the robust infrastructure and services offered by Amazon Web Services (AWS), this creates a powerful and resilient ecosystem.
| Feature | Details |
|---|---|
| Topic Focus | Secure Shell (SSH) for IoT devices over the Internet using Amazon Web Services (AWS) |
| Core Technologies | SSH, IoT Devices, AWS (Amazon Web Services - including but not limited to EC2, VPC, IAM, CloudWatch, etc.) |
| Primary Use Cases | Remote device management, secure access, data encryption, monitoring and alerting, secure communication, secure network architecture |
| Benefits | Enhanced security, centralized management, scalability, cost-effectiveness, improved resilience, ability to connect to the devices over internet |
| Challenges | Key management, secure configuration, potential for misconfiguration, network latency, dependency on the internet connection, AWS costs |
| Target Audience | IoT device developers, network administrators, security professionals, cloud engineers, DevOps engineers, any person want to connect IoT devices over internet using AWS. |
| Relevant Concepts |
|
| Related AWS Services |
|
| External Resources | AWS IoT Official Website |
At its core, the integration hinges on establishing secure, reliable, and efficient connections between IoT devices and a central management point. SSH serves as the secure foundation for this, ensuring that all communications are encrypted and authenticated. This is particularly critical given the often-unsecured nature of many IoT devices, which are frequently deployed with minimal security configurations.
Consider the scenario of a large-scale industrial deployment, perhaps a network of sensors monitoring environmental conditions in a remote location. Without a robust security mechanism, these sensors could be vulnerable to unauthorized access and manipulation. An attacker could potentially compromise the devices, injecting malicious code or altering the data they report. This could have devastating consequences, leading to equipment damage, process disruption, or even environmental hazards. By implementing SSH for remote access, administrators can ensure that only authorized personnel can interact with the sensors, and that all communications are protected from eavesdropping and tampering.
The advantages of using SSH go beyond simple security. It also offers significant benefits in terms of device management and scalability. Using AWS, the management infrastructure can be built to automatically provision and configure new devices, and to monitor the health and performance of existing ones. This centralized approach simplifies the management process, reducing the time and effort required to maintain a large and geographically dispersed IoT network. With the right configuration, administrators can even automate tasks such as software updates, security patching, and configuration changes, further enhancing operational efficiency.
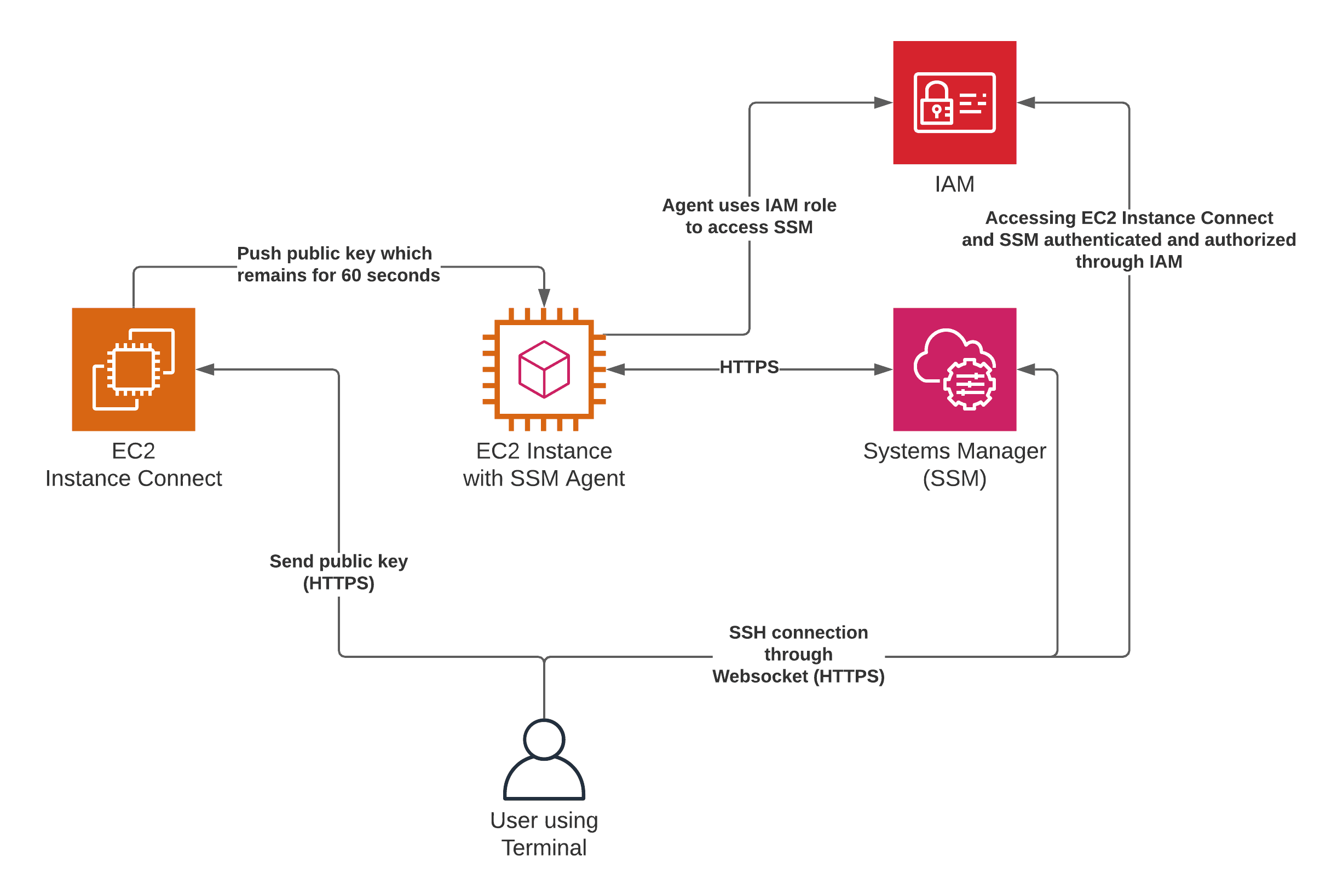
Now, lets examine the specifics of how this integration works. The fundamental principle is to establish a secure SSH connection between the IoT device and a secure, manageable environment, typically hosted on AWS. This often involves the use of a bastion host or a jump server, an instance of an EC2 instance, which acts as a gateway to the private network where the IoT devices reside. The IoT devices themselves are configured to initiate SSH connections to the bastion host, rather than being directly exposed to the public internet. This design offers a number of significant advantages. First and foremost, it significantly reduces the attack surface. By centralizing access through the bastion host, you can control and monitor all SSH connections in a single location, enabling more rigorous security controls.
The process generally unfolds as follows: The IoT device, possessing an SSH client, establishes a connection to the bastion host, which, in turn, can access other resources within the AWS virtual private cloud (VPC) where the IoT devices are located. The connection is secured with SSH keys, ensuring only authorized devices can connect. These keys replace the vulnerable practice of using passwords, greatly enhancing security. This also allows for granular access control using IAM, providing the ability to define who has access to what resources and under what conditions.
Furthermore, AWS provides a wide range of services that complement SSH, greatly expanding its capabilities. CloudWatch, for example, can be used to monitor the health and performance of both the bastion host and the IoT devices, providing real-time insights and alerts if any issues arise. CloudTrail, another powerful service, can log all API calls, providing an audit trail of all actions taken within the AWS environment. By leveraging these services, administrators can gain valuable insights into the overall health and security posture of their IoT deployment. This provides not only the tools to detect, but also to rapidly respond to threats and issues.
The benefits of this architecture are manifold. It allows for secure remote access to devices, even those behind firewalls or NAT devices. The use of SSH tunnels provides a secure channel for data transmission, protecting sensitive information from eavesdropping. It simplifies device management, allowing for centralized configuration, monitoring, and troubleshooting. Also, the utilization of AWS provides scalability and cost-effectiveness, allowing organizations to easily expand their IoT deployments without incurring excessive infrastructure costs.
However, there are challenges to consider. One of the most significant is key management. Securely generating, storing, and distributing SSH keys is critical to the overall security of the system. Mismanagement of these keys can leave the system vulnerable to attack. Another challenge lies in the configuration of the SSH service itself. Incorrectly configured SSH settings can lead to security vulnerabilities. Best practices should be followed to harden the SSH configuration.
Another key area to address is the potential for network latency. The reliance on internet connectivity can introduce delays in communication, particularly in environments with poor network conditions. Therefore, it's crucial to optimize the network infrastructure and the SSH configuration to minimize latency and ensure responsiveness. Moreover, there is a financial aspect. While AWS provides a flexible and cost-effective platform, there are associated costs for compute, storage, and network resources. Organizations should carefully consider these costs when designing and implementing their IoT deployments.
To deploy this architecture, one could start by creating an EC2 instance in their AWS account to serve as the bastion host. This instance should be configured with appropriate security groups to restrict access to only authorized IP addresses and ports. Next, configure the IoT devices to initiate SSH connections to the bastion host. This typically involves installing an SSH client and configuring the device's network settings to point to the bastion host. Once these connections are established, administrators can then use SSH to remotely access the IoT devices, allowing them to perform management tasks.
Beyond the basic setup, the system can be extended with more advanced features. Using SSH tunnels, administrators can securely forward data traffic from the IoT devices to the AWS environment. This is particularly useful for collecting data from the IoT devices and storing it in AWS services such as S3 or DynamoDB. Automated processes can be created, possibly using a combination of AWS Lambda and CloudWatch, which automatically respond to specific events, for example, to troubleshoot a malfunctioning device. The possibilities are endless.
Consider a real-world example of this system in operation. An agricultural company uses sensors to monitor soil moisture, temperature, and other environmental conditions in its fields. These sensors are deployed in remote locations with limited physical access. Using SSH over AWS, the company's engineers can remotely access these sensors, configure their settings, monitor their performance, and troubleshoot any issues that arise. The data collected by the sensors is securely transmitted to AWS, where it is analyzed and used to optimize irrigation schedules, improve crop yields, and reduce water waste. The security offered by SSH, combined with the scalability and analytical capabilities of AWS, is a major asset to the business.
In summary, integrating SSH with IoT devices and AWS offers a compelling solution for securing and managing these devices in a scalable and cost-effective manner. While it's important to be mindful of the challenges such as key management, the benefits, particularly the enhanced security, centralized management capabilities, and the scalability provided by AWS, make this architecture a highly attractive option. As the IoT landscape continues to expand, secure remote access solutions will become increasingly critical. SSH combined with AWS provides a robust and reliable foundation for ensuring the security and operability of these critical connected devices, making it a key tool for businesses in today's digital landscape.
The continuous evolution of both SSH and AWS is also a factor worth considering. Regularly updating SSH clients and server software ensures the latest security patches are applied, mitigating known vulnerabilities. Leveraging the newest features and security services introduced by AWS, like the Identity and Access Management (IAM) and security groups, ensures best practices are in place to enhance the security of the environment. It is therefore crucial to maintain an ongoing process of review, update, and improvement to maintain an efficient and secure system.
Furthermore, think about leveraging infrastructure-as-code (IaC) tools such as Terraform or CloudFormation to automate the deployment and management of the infrastructure. This will not only improve efficiency and consistency but also allow for version control, enabling rollback capabilities if configuration changes cause issues. IaC makes it easier to build, test, and deploy SSH configurations for IoT devices, eliminating manual work and reducing human error. This automation is key for maintaining large-scale deployments.
Looking to the future, the trend of serverless computing, especially with AWS Lambda, can further streamline the architecture. By using Lambda functions to handle tasks such as device provisioning, health monitoring, and security alerts, you can minimize the infrastructure overhead. This combination of serverless with SSH is a powerful and efficient architecture to manage IoT devices, while also keeping costs low. This could be particularly helpful for environments with low device activity where maintaining a constant connection would be overkill.
In conclusion, the synergy between SSH, IoT devices, and AWS provides a formidable strategy to manage and protect IoT deployments across the internet. From secure remote access and centralized management to scalability and cost-effectiveness, the advantages are substantial. While challenges, like key management, should be taken into account, they are manageable with proper planning and execution. As the world becomes increasingly connected, the demand for secure and reliable solutions for IoT devices will only continue to rise. Embracing this architecture will be vital for businesses and organizations that want to take advantage of the opportunities afforded by the IoT landscape.