Remote SSH For IoT: Setup Guide For Devices Behind A Router
How can you securely manage and access your Internet of Things (IoT) devices from anywhere in the world, even when they're tucked behind a router? The ability to establish a secure, remote connection to your IoT devices via Secure Shell (SSH) is not just a technical skill; it's a necessity in todays interconnected world.
The Internet of Things (IoT) has dramatically reshaped our interactions with technology, ushering in an era of seamless connectivity and automation. As IoT devices become increasingly integral to both our personal and professional lives, the capacity to configure and secure these devices through SSH is becoming paramount. This guide will delve into the intricacies of setting up and managing SSH access to IoT devices, particularly those located behind routers, ensuring you can manage your devices securely and efficiently.
Let's examine the fundamental steps needed to establish secure SSH access to your IoT devices. The process begins with SSH keys, which offer a much more secure and convenient authentication method than traditional passwords. Here's a breakdown of the key steps:
- Generate a Key Pair: On your local machine, you'll initiate the process by generating a key pair. This pair consists of a private key, which you keep secure, and a public key, which you'll share.
- Copy the Public Key: The next step involves copying your public key to the authorized_keys file on your IoT device. This file resides in the .ssh directory of the user account you'll be using to access the device.
- Test the Connection: After placing the public key, test the connection to your IoT device. If everything is configured correctly, you should be able to connect without being prompted for a password.
- Single Command Access: With SSH keys in place, you can connect to your devices with a single, streamlined command, making remote management significantly easier.
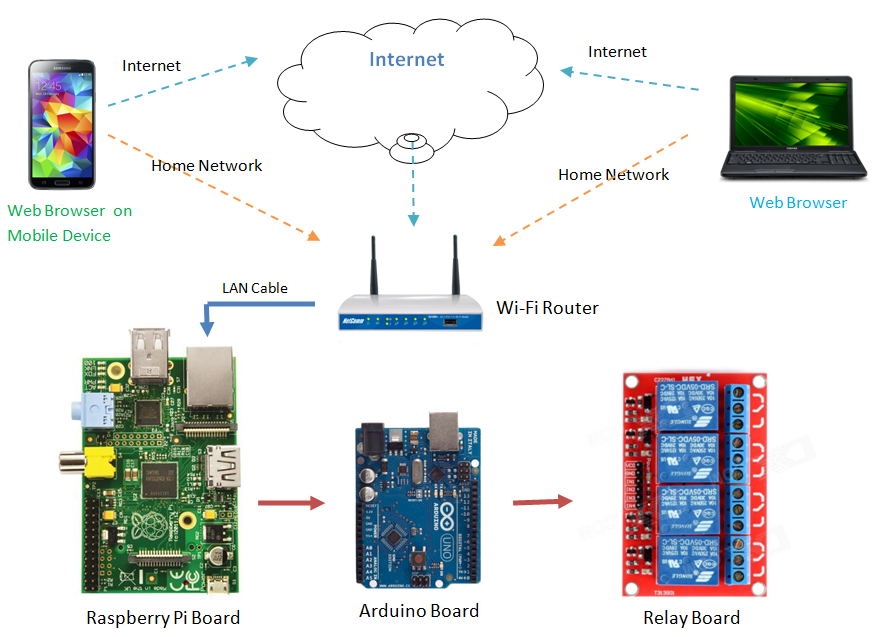
One of the primary hurdles in remotely accessing IoT devices is their location behind a router. Routers, while essential for connecting to the internet, also act as a barrier, preventing direct access to devices on the internal network from the outside world. This is where techniques like port forwarding or the use of reverse proxy tunnels become critical. These methods allow you to bypass the router and establish a secure connection to your IoT devices.
The benefits of remote SSH access are numerous. It empowers you to monitor, control, and troubleshoot your IoT devices from anywhere with an internet connection. This is particularly useful for applications like home automation, remote sensor monitoring, or even managing industrial equipment. Furthermore, remote SSH access provides a secure means to update software, configure settings, and retrieve data from your devices.
However, the importance of security cannot be overstated. Implementing best practices for SSH connections is imperative to safeguard your IoT devices from potential security threats. This includes using strong, unique passwords, regularly updating your devices' software, and being vigilant about potential vulnerabilities. Securing your SSH access is not just about convenience; it is about protecting the sensitive data and functionalities that your IoT devices control.
Platforms like SocketXP offer innovative solutions for remote SSH access to IoT devices. SocketXP provides secure SSH reverse proxy tunnels, allowing you to remotely access and control devices behind NAT routers or firewalls. This approach simplifies the setup process and enhances the overall security of the connection. Using such platforms can significantly streamline the management of your IoT devices, enabling you to focus on your projects and applications.
The landscape of IoT is vast, encompassing a wide variety of devices, from smart home appliances to industrial sensors. The ability to manage and access these devices remotely is becoming increasingly essential. Whether you are a tech enthusiast, an IT professional, or simply a home user looking to automate your life, understanding how to configure and secure SSH access is a critical skill.
Remote SSH access for Raspberry Pi devices, particularly those behind a router, has gained significant traction in the tech community. This is largely due to the Raspberry Pi's versatility and widespread use in IoT projects. The ability to remotely access and control a Raspberry Pi opens up a world of possibilities, from controlling smart home systems to monitoring environmental data. This is achieved through SSH, which allows you to connect securely to your Raspberry Pi from anywhere.
The growing popularity of remote SSH for IoT devices is driven by the increasing reliance on these devices in various aspects of our lives. Whether it's controlling lights and appliances in your home, monitoring environmental conditions, or collecting data from remote sensors, the ability to manage these devices securely and efficiently is essential. By utilizing secure SSH reverse proxy tunnels, you can protect your devices from unauthorized access and ensure the integrity of your data.
When setting up remote SSH access, it is crucial to understand the potential security risks and implement appropriate safeguards. This includes using strong passwords, regularly updating device software, and keeping your SSH configuration secure. By following best practices, you can minimize the risk of unauthorized access and protect your devices from potential attacks.
Managing SSH IoT devices behind a router is a critical skill in todays interconnected world. By understanding the mechanics of SSH and employing the appropriate methods for bypassing router limitations, you can establish secure and reliable remote access to your IoT devices from any location. With the right knowledge and tools, you can fully leverage the potential of the IoT, transforming the way you interact with technology and manage your devices.
In the world of IoT, security is paramount. Always prioritize the security of your connections. This includes using robust passwords, regularly updating your systems, and being mindful of the potential security risks. By adopting a proactive approach to security, you can safeguard your devices and your data. By choosing the right approach, you can connect securely to your IoT devices from anywhere. The key to remote management lies in understanding the basics and deploying secure protocols.
SocketXP provides a platform to remotely access IoT devices that are behind a NAT router or firewall by using secure SSL/TLS VPN tunnels. This functionality enables users to manage their devices securely and efficiently from any location. SocketXP's reverse proxy tunnels facilitate secure SSH connections, which are essential for managing IoT devices remotely.
The approach to IoT management is changing. Its no longer sufficient to simply deploy devices. Its essential to be able to manage them remotely and securely. This requires the implementation of secure protocols. One key aspect is establishing a secure connection to your devices using tools like SSH. This enables you to remotely monitor your devices. Understanding how to establish secure remote access via SSH is a fundamental skill for anyone working with IoT. With proper configuration, you can remotely access and manage your Raspberry Pi from anywhere.
This tutorial covers the basics of SSH, remote access, and the pre-requisites to set everything up. It provides a guide to establishing a secure and reliable connection to your IoT devices from anywhere in the world. Implementing best practices for secure SSH connections is critical in safeguarding your IoT devices from any potential security threats. The core of remote access lies in understanding the benefits and potential applications.
Remote SSH access is more than just a technical term; its a gateway to secure, remote access for smart devices. It is about securing remote access to devices and is a must in today's connected environment. The benefits of setting up remote SSH access are the ability to manage and control IoT devices securely. In this era, devices are becoming integral in both personal and professional environments. Remote SSH access provides a secure way to update software, configure settings, and retrieve data.
This is a critical skill for tech enthusiasts, IT professionals, and home users. By adhering to the steps provided in the tutorial, you can quickly establish a secure and reliable connection. This method is a powerful tool for managing IoT devices.