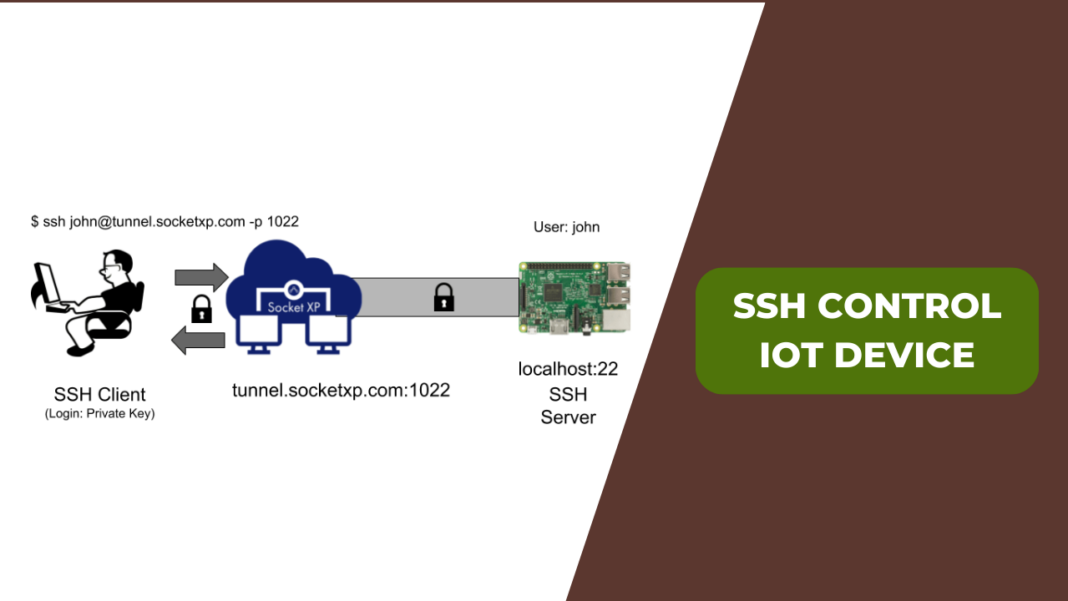
Ssh Connect Iot Device
Is securing your Internet of Things (IoT) devices a constant battle against cyber threats? Understanding how to securely establish an SSH connection to your IoT devices is not just a technical necessity; it's the cornerstone of protecting your data, your network, and ultimately, your peace of mind. The pervasive nature of IoT devices, from smart home appliances to industrial sensors, creates a vast attack surface, making robust security practices paramount. Neglecting this critical aspect can expose sensitive information and enable malicious actors to gain control, causing significant damage.
The process of connecting to an IoT device via SSH (Secure Shell) involves establishing a secure, encrypted connection over a network. This encrypted channel allows for secure command execution, file transfer, and remote access, all vital for managing and maintaining these often-resource-constrained devices. However, the inherent vulnerabilities of many IoT devices, coupled with the potential for misconfiguration, demand a meticulous approach. Simply put, securing your SSH connections to IoT devices is a proactive measure against potential exploits, unauthorized access, and data breaches.
| Attribute | Details |
|---|---|
| Name/Topic | SSH Connection to IoT Devices |
| Definition | Establishing a secure, encrypted connection (SSH) to manage and maintain Internet of Things (IoT) devices remotely. |
| Purpose | Provides secure command execution, file transfer, and remote access, crucial for device management, security patching, and troubleshooting. |
| Importance | Essential for protecting IoT devices from unauthorized access, data breaches, and malicious control, mitigating risks across various applications. |
| Key Components |
|
| Configuration Steps (General) |
|
| Security Best Practices |
|
| Common Issues |
|
| Tools & Technologies |
|
| Examples of Use Cases |
|
| Potential Risks |
|
| Mitigation Strategies |
|
| Related Terms |
|
| Reference | Example Website (Replace with an Actual Relevant Resource) |
The ubiquity of IoT devices, from smart thermostats to industrial control systems, introduces a new dimension to the traditional IT landscape. These devices, often designed with cost and functionality prioritized over security, represent a significant vulnerability if not properly secured. The ability to remotely access and manage these devices is critical for their operation and maintenance, but this access must be secured to prevent exploitation. SSH, as a well-established and widely supported protocol, provides a robust mechanism for this, but only when implemented correctly.
Consider a scenario: a malicious actor gains access to an IoT device on your network. Without a secure SSH connection, they could potentially alter the device's firmware, steal sensitive data, or use the device as a launching pad for further attacks. The consequences range from operational disruption to financial loss and reputational damage. In the context of industrial IoT (IIoT), compromised devices could even pose a threat to human safety. The importance of securing SSH connections to IoT devices, therefore, extends far beyond mere convenience; it is a matter of safeguarding critical infrastructure, sensitive data, and the overall security of the digital environment.
Implementing SSH on an IoT device typically involves several steps. First, you must ensure the device has an SSH server installed and enabled. Many Linux-based IoT devices, such as those running on Raspberry Pi or similar single-board computers, often come with SSH pre-installed. For other devices, you may need to install an SSH server like OpenSSH. The next step is to configure the SSH server, including setting up user accounts and choosing an authentication method. Strong passwords are a basic requirement, but using SSH keys is significantly more secure. SSH keys use cryptographic key pairs to authenticate users, making brute-force attacks much more difficult.
Once the SSH server is set up, you need to configure your network to allow SSH connections. This typically involves ensuring that the firewall on the IoT device, as well as any firewalls or routers in the network path, allows traffic on the SSH port, which is usually port 22. Carefully consider the security implications of opening a port to the internet. If remote access is absolutely necessary, use port forwarding with caution, and limit access to specific IP addresses or networks. Another crucial step is updating the device's firmware. Manufacturers frequently release firmware updates to patch security vulnerabilities, and it is vital to keep your devices up-to-date.
The choice of authentication method is a critical security decision. Using strong passwords, generated and managed securely, is a necessity. However, SSH keys represent a superior approach. SSH keys use a public-private key pair to authenticate a user without requiring a password. This eliminates the risk of password brute-force attacks. Generating and using SSH keys involves several steps. First, you generate a key pair on your local machine using a tool such as `ssh-keygen`. Next, you copy the public key to the authorized_keys file on the IoT device. Then, when you connect to the device, the SSH client uses your private key to authenticate, significantly increasing security.
Securing SSH connections extends beyond just enabling the protocol and setting up user accounts. Regular security audits are essential. These audits should assess the device's configuration, check for vulnerabilities, and verify that security best practices are being followed. Regularly monitoring SSH logs is another vital component. These logs record information about connection attempts, successful logins, and any errors. By monitoring these logs, you can detect suspicious activity, such as repeated failed login attempts that may indicate a brute-force attack. Network segmentation, the practice of separating your IoT devices from other network segments, is also highly recommended. This limits the potential damage from a security breach. If an attacker compromises an IoT device, they will be isolated to that segment, preventing them from easily accessing other critical parts of your network.
When implementing SSH on IoT devices, careful attention to detail is critical. Default configurations often represent significant security risks. For example, default usernames and passwords should be changed immediately. Failure to do so leaves your devices vulnerable to easily-exploitable attacks. The principle of least privilege should also be applied. Users should only be granted the minimum necessary permissions to perform their tasks. This reduces the impact if an account is compromised. Moreover, consider the physical security of the devices. Physical access to a device can bypass many security measures. Keep devices secure and protected from unauthorized access.
The ongoing evolution of IoT technology introduces new security challenges. As devices become more sophisticated and interconnected, the potential attack surface expands. Staying informed about the latest security threats and best practices is crucial. This includes subscribing to security advisories, reading industry publications, and participating in relevant training. Consider the specific characteristics of your IoT environment. Different types of devices and applications have different security requirements. A smart home environment will have different needs compared to an industrial automation system. Tailor your security measures to fit the particular risks associated with your deployment.
Troubleshooting SSH connections to IoT devices often involves common issues. One frequent problem is an incorrect IP address or hostname. Double-check the device's network configuration to ensure you are using the correct address. Firewall issues are also common. Make sure the firewall on both the device and your network allows SSH traffic on port 22 (or whatever port you have configured). Incorrect credentials are another frequent cause of connection failures. Verify that you are using the correct username and password, or that your SSH key is properly configured. Occasionally, the SSH service itself may not be running on the IoT device. Check the devices system logs to confirm the service is active. Compatibility issues can arise if you are using an outdated SSH client or server. Ensure that both are up-to-date.
The tools and technologies used to secure and manage SSH connections on IoT devices are diverse. OpenSSH is the most widely used SSH implementation. It is available for most operating systems, including Linux, Windows, and macOS. PuTTY is a popular SSH client for Windows users. Tools like `ssh-keygen` are essential for generating SSH keys. Network monitoring tools such as Wireshark and tcpdump can be used to analyze network traffic and troubleshoot connection problems. Firewall software, such as iptables or ufw on Linux systems, allows you to control network access and enforce security policies. Furthermore, IoT device management platforms, such as AWS IoT or Azure IoT Hub, often provide features for secure remote access and management, including SSH tunneling or integrated security features. Consider using these platforms for simplified management of your fleet of IoT devices.
The potential risks associated with insecure SSH connections on IoT devices are significant. Brute-force attacks, where attackers attempt to guess passwords by trying numerous combinations, are a constant threat. Man-in-the-middle attacks, where attackers intercept communication between the client and server, can compromise the confidentiality of data. Malware infections, which can exploit vulnerabilities in the device's software, can give attackers complete control. Unauthorized access, allowing attackers to access and modify the device's settings or data, is a major concern. Data breaches, where sensitive information is stolen, can have serious consequences. Mitigating these risks requires a multi-layered approach, including the use of strong authentication, regular firmware updates, network segmentation, and firewalling.
The application of secure SSH connections extends across numerous use cases. Remote firmware updates allow for secure software updates over the network, reducing the need for physical access. Configuration management enables you to remotely configure device settings, saving time and effort. Troubleshooting capabilities permit remote diagnosis and resolution of issues without physical presence. Data collection allows for the secure retrieval of data from devices for analysis and monitoring. Security hardening involves implementing security best practices on each device, ensuring its overall protection. By utilizing these features, you can improve the efficiency of your IoT operations and increase your network security posture.
In conclusion, securing SSH connections to IoT devices is a critical aspect of modern cybersecurity. It demands a proactive approach that includes proper configuration, regular security audits, and a commitment to staying informed about the latest threats and best practices. By implementing these measures, you can mitigate the risks associated with unsecured IoT devices and safeguard your valuable data, infrastructure, and peace of mind. Failing to take these precautions leaves you exposed to a range of potential cyberattacks, from simple intrusions to complex breaches, highlighting the vital necessity of secure SSH connections in the world of IoT.