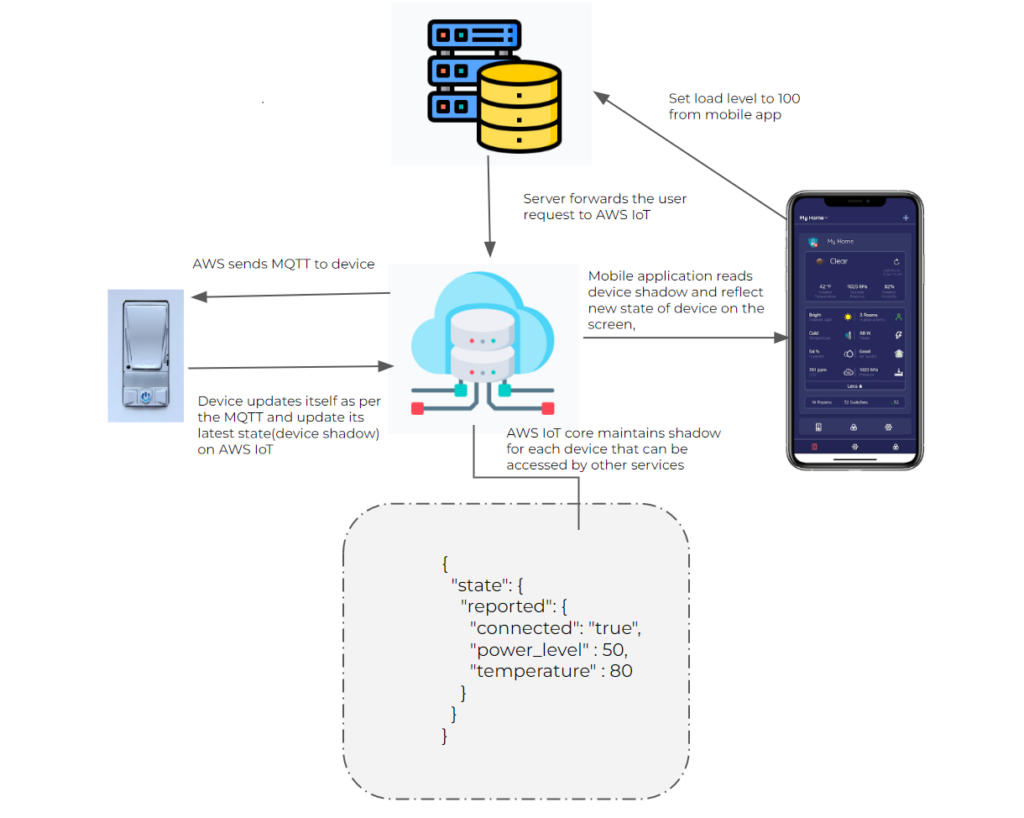
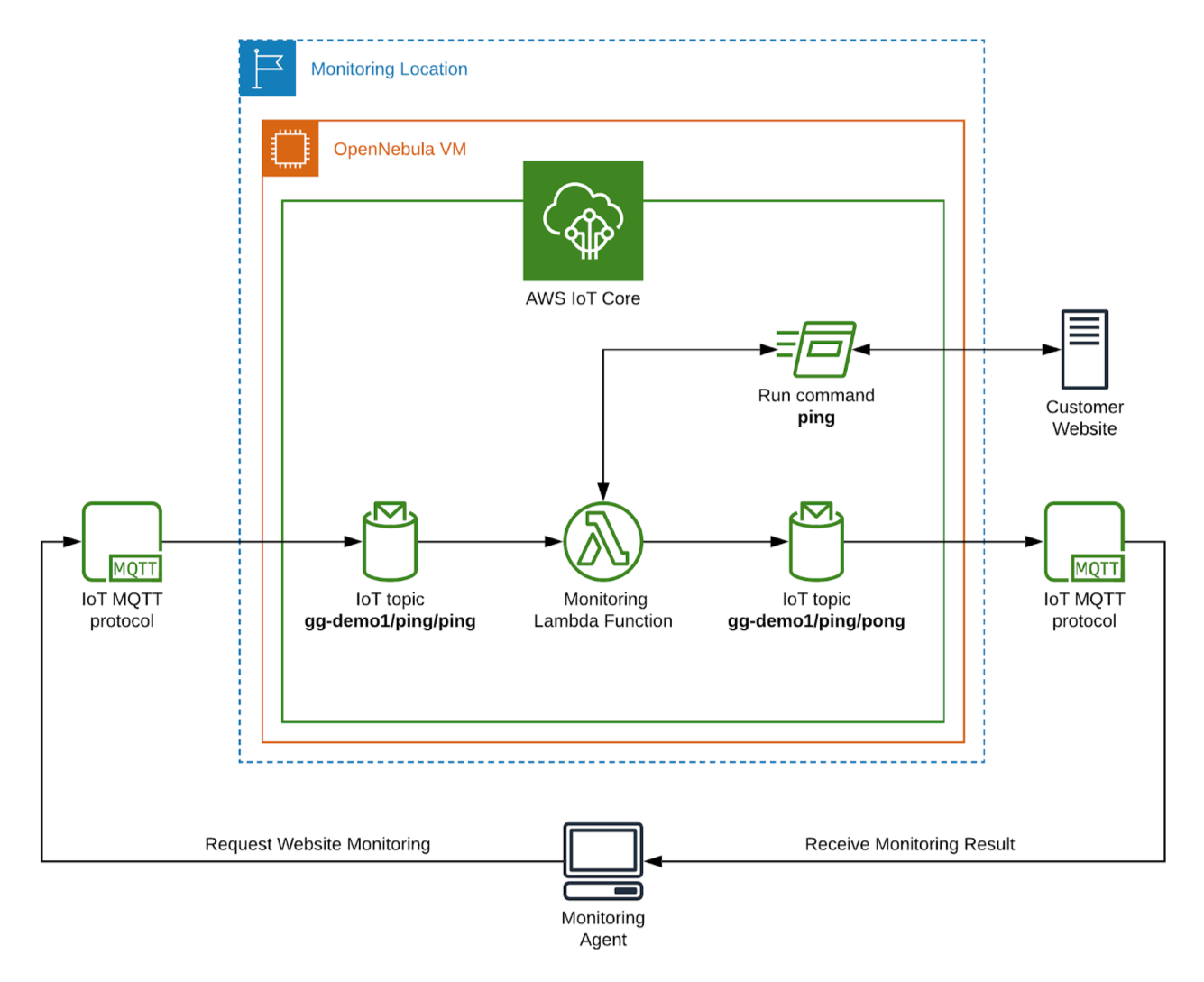
How To: Monitor IoT Devices Behind Firewall AWS - Guide
Can you truly secure your Internet of Things (IoT) devices deployed behind an AWS firewall, and if so, how comprehensive can that security actually be? The ability to effectively monitor IoT devices residing behind a firewall within the AWS ecosystem is not just a technical necessity; it is a fundamental pillar supporting the safety, stability, and longevity of any IoT deployment. Failure to implement robust monitoring can expose critical vulnerabilities, leading to data breaches, operational disruptions, and significant financial repercussions.
The core challenge stems from the nature of IoT devices themselves. Often resource-constrained, they may lack the processing power or inherent security features needed for comprehensive self-monitoring. Furthermore, their communication protocols, often designed for efficiency rather than security, can introduce exploitable vulnerabilities. Coupled with the complexity of AWS services, configuring and maintaining a secure and observable environment demands a nuanced understanding of network architecture, security best practices, and the capabilities of various AWS tools.
The task of effectively monitoring IoT devices behind an AWS firewall is a multifaceted endeavor, requiring a strategic approach that encompasses several key areas. Firstly, it involves the establishment of robust network segmentation. This means carefully defining zones within your network to isolate different types of devices and applications. IoT devices should ideally reside in a dedicated segment, protected by firewalls that control inbound and outbound traffic. AWS offers various solutions for network segmentation, including Virtual Private Clouds (VPCs), security groups, and network access control lists (ACLs). Each of these tools plays a crucial role in restricting access and limiting the attack surface.
Secondly, a strong emphasis on logging and audit trails is paramount. Every network activity, device interaction, and security-related event should be meticulously logged. This includes capturing data about network traffic, device behavior, and authentication attempts. AWS CloudWatch is a powerful service for collecting, analyzing, and monitoring logs. It integrates seamlessly with other AWS services, allowing you to create dashboards, set up alerts, and gain valuable insights into your IoT environment. Proper logging enables the identification of suspicious activities, security breaches, and performance bottlenecks. Regular audits of your logs are a critical component of maintaining a secure posture.
Thirdly, continuous vulnerability assessments are essential. The landscape of security threats is constantly evolving, and new vulnerabilities are discovered regularly. Regular vulnerability scanning helps identify weaknesses in your IoT devices and their associated software. AWS provides services like Amazon Inspector to scan your resources for security vulnerabilities. You can also leverage third-party security tools for more specialized scanning and analysis. The goal is to proactively identify and remediate any potential weaknesses before they can be exploited by attackers. This includes patching software, updating firmware, and hardening device configurations.
Fourthly, consider the use of intrusion detection and prevention systems (IDS/IPS). These systems are designed to detect and respond to malicious activities in real-time. An IDS monitors network traffic for suspicious patterns, while an IPS takes active steps to block or mitigate threats. AWS offers services like GuardDuty and Network Firewall that can be used to implement IDS/IPS capabilities within your IoT environment. Setting up appropriate rules and alerts allows you to respond quickly to any detected attacks, limiting potential damage.
Finally, effective monitoring often involves the integration of multiple tools and services. This is where the true power of AWS comes into play. You can combine the capabilities of CloudWatch, GuardDuty, Network Firewall, and other services to create a comprehensive monitoring solution. For example, you might configure CloudWatch to collect logs from your devices, GuardDuty to detect unusual activities, and Network Firewall to block suspicious traffic. By centralizing your monitoring and alerting, you can gain a holistic view of your IoT environment and quickly respond to any threats.
Implementing these strategies requires careful planning and execution. Its important to start with a clear understanding of your security goals and risk tolerance. You should also thoroughly assess the capabilities of your IoT devices and the specific requirements of your application. A well-designed monitoring solution should be tailored to your unique needs and continuously adapted as your environment evolves. This dynamic approach ensures that your monitoring capabilities remain effective in the face of changing threats.
The challenges in monitoring IoT devices behind a firewall on AWS are numerous, yet resolvable. The inherent limitations of many IoT devices in terms of processing power and security features present an initial hurdle. These devices frequently operate on constrained resources and may lack the capacity for sophisticated security measures. This forces a reliance on the AWS infrastructure and its security services to compensate for device-level vulnerabilities. Another obstacle is the diversity of IoT device manufacturers and the heterogeneous nature of their security practices. This variability makes it difficult to standardize security configurations and monitoring approaches. Each device might use a different communication protocol or have its own set of vulnerabilities.
Furthermore, managing the sheer volume of data generated by a large number of IoT devices can be overwhelming. The continuous flow of data from these devices, including logs, metrics, and performance data, requires efficient processing and storage. Analyzing this vast quantity of information to identify patterns, anomalies, and potential threats demands sophisticated tools and techniques. Finally, the dynamic nature of IoT deployments presents an ongoing challenge. Devices may be added, removed, or updated frequently, necessitating constant adjustments to your monitoring configurations. This dynamic environment requires an agile and scalable approach to monitoring, allowing you to adapt to changes and maintain a consistent level of security.
To effectively meet these challenges, consider specific steps and tactics. Establish clear security objectives and policies, aligning them with your business needs and risk tolerance. Determine what you aim to protect, what potential threats exist, and how you will measure the effectiveness of your security measures. Conduct a thorough risk assessment of your IoT environment. Identify the vulnerabilities in your devices, networks, and applications, assessing the likelihood and potential impact of each threat. Prioritize your security efforts based on these risks.
Furthermore, carefully select your monitoring tools. Choose tools and services that are appropriate for your specific IoT environment, taking into account factors like scalability, compatibility, and ease of integration. AWS provides a wide range of services, so carefully consider the services that best fit your needs. Design a detailed monitoring plan. Outline the specific metrics, logs, and alerts you will use to monitor your IoT devices. Clearly define how you will collect, analyze, and respond to the data. Your plan should cover all aspects of your monitoring program, from data collection to incident response. Ensure that your network is properly segmented to limit the attack surface. Separate your IoT devices from other parts of your network using VPCs, security groups, and network ACLs. This limits the impact of a potential breach. Implement strong authentication and authorization mechanisms. Use robust authentication methods like multi-factor authentication (MFA) to protect access to your IoT devices and AWS resources. Enforce the principle of least privilege, granting users only the necessary permissions.
Deploy security solutions designed to protect against specific threats. Use an IDS/IPS to detect and respond to suspicious network activity. Implement vulnerability scanning to identify and fix security weaknesses. Use AWS WAF to protect your web applications from common web exploits. Automate security tasks whenever possible, such as patching, configuration management, and incident response. Automation reduces the potential for human error and allows you to respond quickly to threats. Train your team. Ensure that your team has the necessary skills to monitor your IoT environment, analyze data, and respond to security incidents. Provide ongoing training to keep your team up-to-date on the latest threats and security best practices. Regularly test your monitoring solution. Conduct penetration testing and red team exercises to evaluate the effectiveness of your security measures and identify any weaknesses. Regularly review and update your security policies and procedures. Adapt your security practices to reflect the changing threat landscape and your organization's evolving needs. Establish a clear incident response plan. Define the steps you will take to respond to a security incident, including how you will contain the breach, investigate the cause, and recover from the attack.
AWS offers a comprehensive suite of services specifically designed to aid in the monitoring of IoT devices. These services provide capabilities for data collection, analysis, and response. The core of AWS's IoT monitoring capabilities rests on the services discussed earlier: CloudWatch, GuardDuty, Network Firewall, and Inspector. CloudWatch serves as the central hub for collecting and analyzing logs and metrics, offering tools for setting up dashboards and alerts. GuardDuty provides threat detection by analyzing network traffic and identifying suspicious activities using machine learning algorithms. Network Firewall acts as an advanced firewall for traffic inspection and intrusion prevention, and Inspector assists with identifying software vulnerabilities. These services work together, providing a layered approach to security and enabling a detailed view of the entire IoT environment.
In addition to these core services, AWS offers additional options for enhancing IoT device monitoring. AWS IoT Core itself provides features for managing and securing IoT devices. It enables you to collect device data, manage device identities, and implement security policies. AWS IoT Device Defender helps to audit device configurations and monitor device behavior, ensuring devices are operating securely. AWS IoT Analytics enables you to store, process, and analyze large volumes of IoT data, gaining insights into device performance and behavior. By leveraging these combined tools, organizations can create a strong monitoring environment tailored for IoT deployments.
Specific examples of monitoring configurations in the AWS environment highlight the versatility of the platform. For example, you can configure CloudWatch to collect logs from your IoT devices, including metrics related to device performance, network connectivity, and security events. These logs can be analyzed in real-time to identify any anomalies or potential security threats. You can also use GuardDuty to monitor network traffic for suspicious activities, such as attempts to access unauthorized resources or malicious communication patterns. GuardDuty uses machine learning to detect these threats and sends alerts when suspicious behavior is identified. You can set up Network Firewall rules to block malicious traffic and prevent unauthorized access to your IoT devices. This could include blocking traffic from known malicious IP addresses or restricting access based on geographic location. You can use Inspector to regularly scan your devices for security vulnerabilities, such as missing software patches or misconfigured settings. Inspector will identify any vulnerabilities and provide recommendations for remediation.
The best practices for implementing a robust monitoring solution within the AWS framework center on the need for continuous vigilance and proactive measures. Start with a clear understanding of your security requirements and risk tolerance. Identify the critical assets in your IoT environment and the potential threats that could compromise them. Define the metrics and logs you will monitor to detect security incidents. Implement proper network segmentation to isolate your IoT devices and limit the impact of a potential breach. Ensure that your devices are placed within a dedicated VPC with security groups and network ACLs configured to control network traffic. Use strong authentication and authorization mechanisms to protect access to your devices. Implement multi-factor authentication (MFA) to protect access to your AWS resources and ensure only authorized users can access your devices. Configure your monitoring tools to collect the necessary data and generate alerts. Set up alerts for unusual network activity, suspicious device behavior, and any security incidents. Continuously review and improve your monitoring configurations. Adjust your monitoring settings as your environment changes and update your rules and alerts to address new threats.
In the evolution of IoT security, the emphasis is increasingly placed on proactive, automated, and scalable solutions. The growing sophistication of cyber threats, coupled with the expanding scale of IoT deployments, requires organizations to adopt a more sophisticated approach to security. This includes the use of machine learning and artificial intelligence to detect and respond to threats in real-time. This shift also focuses on automating security tasks, such as patching, configuration management, and incident response, to reduce human error and improve efficiency. Scalability is another critical consideration, as IoT deployments often involve thousands or even millions of devices. Monitoring solutions must be able to scale to accommodate the growing number of devices and the increasing volume of data generated. The focus is on creating a more resilient and proactive approach to IoT security, which emphasizes continuous monitoring, automation, and scalability.
Looking forward, the future of monitoring IoT devices behind an AWS firewall will likely involve increased integration of machine learning and artificial intelligence to detect and respond to threats more effectively. This includes advanced threat detection, anomaly detection, and automated incident response. The development and use of more sophisticated threat intelligence feeds will be essential for staying ahead of emerging threats. The expansion of edge computing will create opportunities for localized monitoring and security. As data is processed closer to the device, more immediate threat detection and response will be possible. Greater focus on security by design will also emerge. Security will be integrated into the design and development of IoT devices and applications. This will lead to more secure devices and reduce the need for retroactive security measures. The ultimate goal is a future where IoT deployments are inherently secure, with continuous monitoring and automated responses to evolving threats. The emphasis will be on building a robust, adaptable, and automated security framework to ensure the continued growth and success of IoT applications.