Secure VNC Connections: Setup Guide For Beginners
Are you tired of the inherent vulnerabilities that plague your remote access connections? Securing your VNC (Virtual Network Computing) connections is not just a recommendation; it's a necessity in today's digital landscape, safeguarding your data and maintaining the integrity of your systems. Failure to do so leaves you exposed to a myriad of threats, from eavesdropping to complete system compromise. We delve into the critical steps required to establish secure VNC connections, ensuring your remote access is both functional and fortified against malicious actors.
The convenience of VNC, which allows you to control a computer remotely over a network, often overshadows the potential security pitfalls. By default, VNC transmits data unencrypted, making it susceptible to interception by anyone monitoring the network traffic. This means that passwords, sensitive documents, and other critical information can be easily stolen. Furthermore, VNC servers can be vulnerable to brute-force attacks, where attackers attempt to guess passwords. This article will guide you through the essential configurations needed to mitigate these risks, protecting your valuable data.
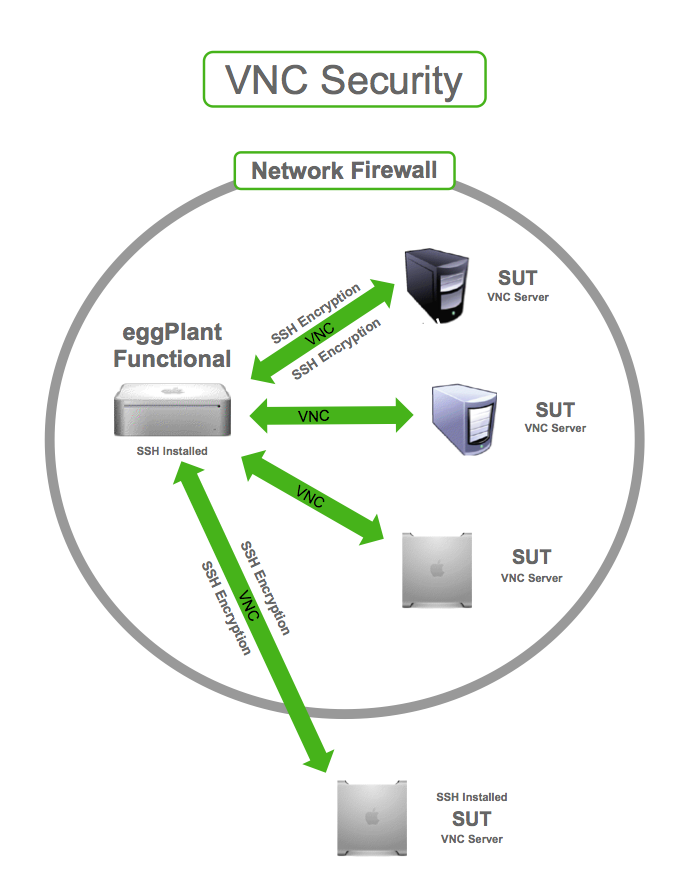
The fundamental principle of securing VNC connections lies in encryption. Without encryption, all data transmitted between the client and the server, including passwords and the screen content, is sent in plain text. Anyone intercepting this traffic can easily read the information. Several methods provide encryption for VNC, and they are crucial in establishing a secure connection.
One of the most effective methods is using SSH (Secure Shell) tunneling. SSH creates an encrypted tunnel between the client and the server, through which all VNC traffic is routed. This ensures that all data is encrypted and protected from eavesdropping. Another approach involves using a VNC server that supports built-in encryption, such as those using TLS/SSL. TLS/SSL offers robust encryption, safeguarding the data transmitted between the client and the server.
Configuring SSH tunneling for VNC requires a few steps. First, ensure that SSH is enabled on the VNC server machine. Next, establish an SSH connection from your client machine to the server. This can be done using an SSH client such as PuTTY on Windows or the SSH command on Linux and macOS. The command typically looks like this: `ssh -L :localhost: @`. In this command, `` is the port on your client machine that VNC traffic will be forwarded to (e.g., 5900), `` is the VNC server port (usually 5900, 5901, etc.), `` is your username on the server, and `` is the IP address of the VNC server. Once the SSH tunnel is established, you can connect to the VNC server using a VNC client, specifying `localhost:` as the server address. This ensures that all VNC traffic is securely tunneled through the SSH connection.
Employing a VNC server with built-in encryption offers another layer of security. Popular VNC servers like TigerVNC and TightVNC often support TLS/SSL encryption. To enable encryption, youll need to configure the server settings, typically involving creating and specifying an SSL certificate. Once configured, your VNC client must also support SSL and be configured to connect using the encrypted connection. This method simplifies setup compared to SSH tunneling but is contingent on the VNC servers support and configuration.
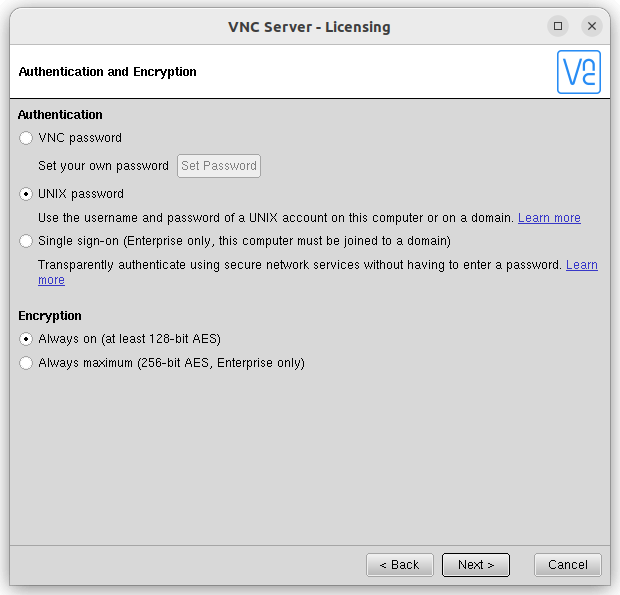
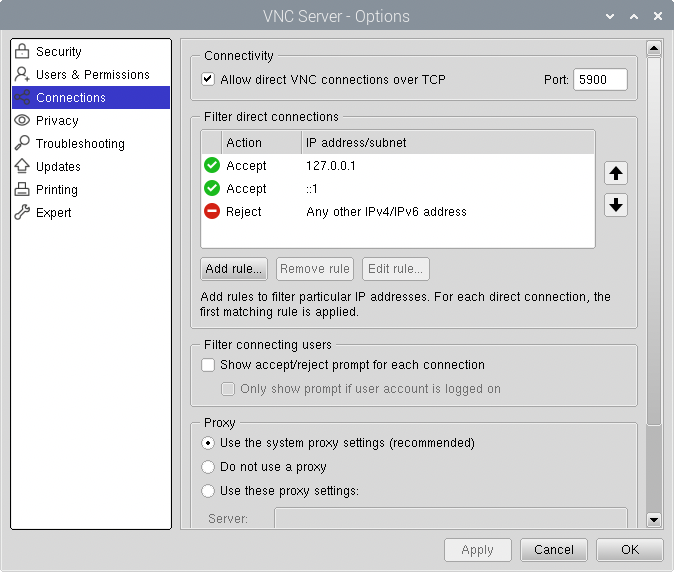
Beyond encryption, authentication is another critical element of securing VNC. Weak or default passwords are a major security risk. Implementing strong, unique passwords and changing them regularly is essential. Consider using multi-factor authentication (MFA), if supported by your VNC server software. MFA requires a second form of verification, such as a code from an authenticator app or a security key, in addition to the password. This adds an extra layer of security, even if the password is compromised. Furthermore, restrict access by IP address, allowing connections only from trusted networks or specific IP addresses. This reduces the attack surface by preventing unauthorized access from external sources.
Firewalls also play a vital role in protecting VNC servers. Configure the firewall to allow incoming connections only on the ports required for VNC (typically 5900+). Close any unnecessary ports to reduce the attack surface. Regularly update the firewall rules to reflect any changes in your network configuration. Regularly monitor the logs to detect any suspicious activities, such as failed login attempts or unauthorized access attempts. Analyze these logs to identify potential security threats and take appropriate action.
Regularly update the VNC server software and the operating system on the server machine. Security patches are released to address vulnerabilities. Failing to apply these updates leaves your system vulnerable to exploits. Furthermore, disable any unnecessary services on the server to reduce the attack surface. The fewer services running, the fewer potential entry points for attackers. Consider using a separate, dedicated machine for the VNC server, rather than running it on a machine used for other purposes. This isolates the VNC server, limiting the potential damage if it is compromised.
A comprehensive security assessment should be part of the ongoing maintenance. Conduct penetration testing to identify vulnerabilities in your VNC setup. This involves simulating attacks to identify weaknesses and provide recommendations for improvement. Regularly review your security policies and procedures to ensure they are up-to-date and effective. Training for all users who access VNC is essential. They need to understand the security risks and follow best practices, such as using strong passwords and recognizing phishing attempts.
In the face of ever-evolving cyber threats, remaining vigilant is paramount. Periodically review and update your security configuration and policies, ensuring they align with current best practices. Stay informed about the latest security threats and vulnerabilities, and take proactive measures to protect your systems. Securing your VNC connections is not a one-time task but an ongoing process. A proactive and informed approach to security is crucial for protecting your data and maintaining the integrity of your systems.